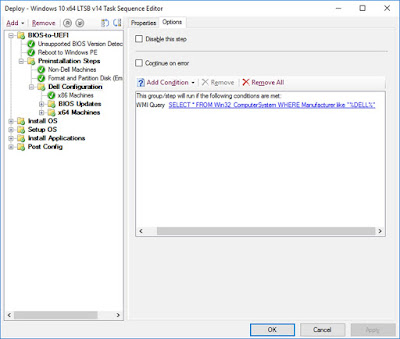
NLA in Windows 10 uses 3 different network profiles: Domain, Public and Private. Windows assigns the network connection to one of these profiles when a new network is discovered. It’s important to know the differences because this actually provides us with a really powerful tool to lock down our machines using the built in Windows Firewall.
How the appropriate location is determined
Domain
Microsoft explain that Windows checks the connection specific DNS name against “HKEY_Local_Machine\Software\Microsoft\Windows\CurrentVersion\Group Policy\History\NetworkName” (although on my test machine this was an empty key but “HKEY_Local_Machine\Software\Microsoft\Windows\CurrentVersion\Group Policy\History\MachineDomain” contained the domain DNS name). If this matches and the machine is able to go on and contact a Domain Controller via LDAP, then you are assigned the Domain profile.Public vs Private
This is the bit most people get confused about and it is a distinction which appeared from Windows Vista onwards (in XP the profiles were Domain and Standard). The way that the location is determined is via the prompt that you receive when connecting to a new network ie “Do you want to allow your PC to be discoverable by other PCs and devices on this network?”. Selecting “Yes” assigns the Private profile whilst “No” assigns the Public profile.It’s useful to know of this distinction as it will allow you to configure specific rules on the firewall which will behave differently depending on whether you are connected to a trusted or untrusted network.